Google Authenticator PAM Available in Ubuntu 11.10
Google provides an application called Google Authenticator for various smartphone platforms. Using it, you can secure your Google account against hackers by logging in with a frequently-changing code from your phone alongside your regular password. Only your phone and Google know the key needed to generate the code sequence. This provides two factor authentication; you need to know your password as well as have your phone.
Google Authenticator is open source, and build upon open standards. The project provides a pluggable authentication module (PAM) which allows the Authenticator to be used to log into Linux systems (without any involvement from Google’s servers). This is useful for providing additional security for remotely-accessed servers. If for whatever reason you don’t want to use a public key authentication for SSH, you can use Google Authenticator instead, although you can’t use both at once.
The Ubuntu 11.10 repository now includes the PAM for Google Authenticator in the
package libpam-google-authenticator.
sudo apt-get install libpam-google-authenticator
If you’re running an older Ubuntu release, you’ll have to download and compile it yourself.
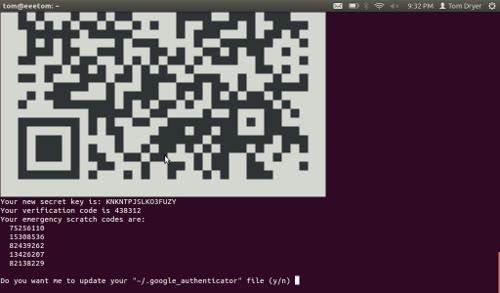
After installing, run the google-authenticator application as the user you
will access remotely. This will create a key and display a QR code which you can
scan using the smartphone app. You will also get some emergency codes for when
you don’t have your phone.
Now you will need to enable the PAM for SSH login attempts. Open the file
/etc/pam.d/sshd, and add this line:
auth required pam_google_authenticator.so
Next, open /etc/ssh/sshd_config, and change or add the
ChallengeResponseAuthentication line so it reads:
ChallengeResponseAuthentication yes
Restart SSH to make the configuration change take effect:
sudo service ssh restart
If you’re setting this up on a remote server, keep your current SSH session open so you can revert the changes if needed. Try to SSH to the system, and you should be prompted for the password and verification code before you are admitted.
Credit to blog.theroux.ca for the instructions on hooking the PAM up to SHH.
If you’re feeling adventuresome, you can even add the auth required
pam_google_authenticator.so line from above to other files in pam.d. Adding
it to lightdm will cause the login screen to prompt for the verification code.
Adding it to login will cause the virtual terminals to also ask for it (but I
couldn’t get them to accept a code on my system).
Google Authenticator is useful for SSH servers, but on a desktop or laptop I’m not sure it’s good for much other than impressing your friends. Anyone with physical access to the system can extract the authenticator key from the hard drive. Even if the drive is encrypted, the key has to remain in the clear in order to validate codes.
Archived Comments
Tom
I was only considering a hypothetical setup where the disk is encrypted until you provide a code. There would have to be an unencrypted partition for the key, which of course would make the protection useless.
calvinium
For Ubuntu 11.10, adding “auth required pam_google_authenticator.so” before the “@include common-auth” worked fine for me for vt’s
calvinium
er, I neglected to say the changes were in the /etc/pam.d/login file
jay
“Even if the drive is encrypted, the key has to remain in the clear in order to validate codes.”
Where exactly is the key going to be stored in the clear if the drive’s encrypted? Using dm-crypt via the alternate installer, the only unencrypted space I know of is the GRUB partition.